
The Role of Network Segmentation in Preventing Lateral Attacks
Network segmentation plays a crucial role in preventing lateral attacks by isolating systems and limiting access to critical data within a network. It helps confine breaches to specific segments, preventing attackers from easily moving through the network. While it is not a complete solution, network segmentation significantly enhances overall network security, particularly when combined with other practices like strong access controls and continuous monitoring. Adopting segmentation techniques
✨ Raghav Jain
Introduction
Cybersecurity threats are constantly evolving, with attackers becoming more sophisticated in their methods. One of the most dangerous tactics they use is lateral movement—once they’ve breached an initial point of entry in a network, they move laterally to access other systems or data. Lateral attacks can lead to significant damage, such as data theft, system compromise, or complete network disruption. In this context, network segmentation emerges as a vital strategy in preventing lateral attacks and limiting the extent of potential damage. This article explores the role of network segmentation in cybersecurity, its benefits, challenges, and best practices for preventing lateral attacks.
Network segmentation plays a crucial role in preventing lateral attacks by dividing a network into smaller, isolated segments, making it significantly harder for attackers to move freely within an organization’s infrastructure after a breach. Lateral attacks, in which cybercriminals exploit a vulnerability to gain initial access to a network and then move across the network to escalate privileges or steal data, pose a substantial threat to businesses. Once an attacker compromises one point of entry, without segmentation, they can easily move from one system to another, often undetected. By implementing network segmentation, organizations create barriers that limit the attacker’s ability to traverse the entire network, containing the potential damage and reducing the attack surface. Each segment in a segmented network can be isolated based on specific functions, users, or data types, enforcing access controls and limiting communication between segments to only what is necessary for business operations. This approach helps minimize the lateral movement of attackers by making it more challenging for them to reach other systems or sensitive information. With a properly segmented network, even if an attacker compromises one segment, they may only have access to a limited portion of the network, making it easier to detect and isolate the threat. Network segmentation also facilitates more granular monitoring and auditing, as traffic between segments can be closely inspected for suspicious activity, anomalies, or unauthorized access attempts. Additionally, segmentation enhances the effectiveness of firewalls, intrusion detection systems, and other security tools, as each segment can be protected by its own set of security policies. For instance, sensitive data segments might have stricter security controls than less critical parts of the network, ensuring that highly valuable information is safeguarded more rigorously. Implementing segmentation also means that even if one part of the network is compromised, security teams can quickly isolate and contain the breach, preventing it from spreading across the network. This containment can significantly reduce the time an attacker spends within the network, thereby lowering the risk of further exploitation or data exfiltration. Furthermore, segmentation allows organizations to implement the principle of least privilege, ensuring that users and devices only have access to the resources they need for their specific role, reducing the likelihood of lateral movement. It also aids in compliance with data protection regulations, such as the GDPR, which often require sensitive data to be isolated and protected against unauthorized access. However, implementing network segmentation is not without its challenges. Organizations must carefully plan the segmentation strategy to ensure it aligns with business requirements while providing effective security. Over-segmentation can lead to network complexity and performance issues, while under-segmentation may leave gaps that attackers can exploit. Effective segmentation requires ongoing monitoring and management to ensure that security controls remain intact as the network evolves. Moreover, network segmentation must be coupled with other security measures, such as endpoint protection, regular patching, and user training, to create a multi-layered defense against lateral attacks. While segmentation significantly improves network security, it is not a silver bullet and should be considered as part of a broader cybersecurity strategy that includes threat intelligence, vulnerability management, and incident response. It is essential for organizations to continuously assess and update their segmentation approach in response to emerging threats and changes in their infrastructure. Additionally, organizations must ensure that network segmentation is integrated with other security technologies like zero-trust models, which assume that no device, user, or system can be trusted by default, further enhancing the security posture against lateral movement. By adopting network segmentation, organizations can not only reduce the risks associated with lateral attacks but also gain greater visibility and control over their network infrastructure, which ultimately leads to a more secure and resilient IT environment.
What is Network Segmentation?
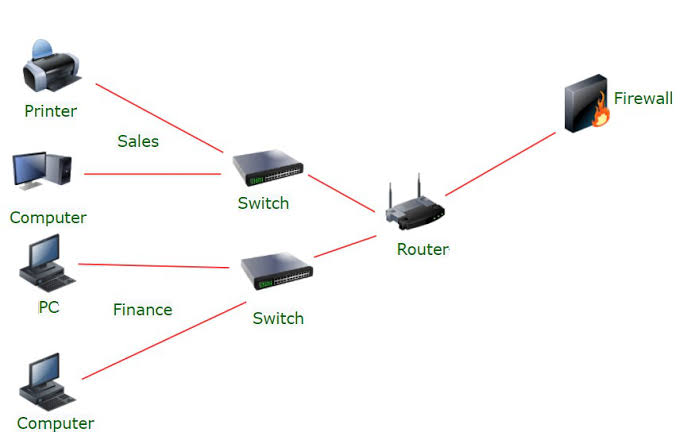
Network segmentation is the practice of dividing a computer network into smaller, isolated segments or sub-networks. Each segment operates as an individual network, with its own security controls and protocols. The goal of network segmentation is to reduce the attack surface by restricting access between different parts of the network and limiting the movement of potential threats.
Network segmentation is crucial for controlling the flow of sensitive data and ensuring that even if a breach occurs, the attacker cannot freely navigate through the entire network. By isolating critical systems and sensitive information, segmentation makes it more difficult for cybercriminals to move laterally once they’ve gained initial access to a network.
Understanding Lateral Attacks and Their Impact
Lateral attacks, or lateral movement, refer to the process by which cybercriminals expand their reach within a compromised network. After breaching an initial entry point, attackers use tools, techniques, and exploits to move across the network, gaining access to additional resources, systems, and data. This enables them to escalate privileges and potentially cause widespread damage before being detected.
Lateral attacks are dangerous because they can remain undetected for extended periods. Once inside, attackers typically avoid triggering traditional perimeter defenses. They can use stolen credentials, take advantage of vulnerabilities, or exploit weak network configurations to navigate through the organization’s internal systems. Lateral attacks can lead to:
- Data Breaches: Accessing and stealing sensitive data such as customer information, intellectual property, or financial records.
- Ransomware Spread: The malware may quickly move across the network, locking files and demanding ransom.
- Privilege Escalation: Attackers gain higher-level access to systems or administrative controls, further increasing their ability to cause damage.
- Widespread Network Disruption: Systems may be corrupted, compromised, or brought down, impacting business continuity.
Given these risks, it is essential to have strong defenses in place to prevent and contain lateral attacks.
How Network Segmentation Helps Prevent Lateral Attacks
Network segmentation serves as an effective security measure to prevent lateral attacks by limiting the extent to which attackers can move within a network. Below are the key ways in which segmentation can mitigate lateral movement:
1. Containing the Attack
Once an attacker gains access to a segment of the network, segmentation prevents them from easily moving to other parts of the network. By creating barriers between critical systems, databases, and general workstations, the attack is confined to the compromised segment. This containment drastically reduces the potential damage and limits the number of systems that need to be investigated, patched, or restored.
2. Limiting Access to Sensitive Information
Network segmentation allows organizations to segregate sensitive data and systems from less critical infrastructure. For example, finance, human resources, or customer data can be isolated in separate segments that require more stringent access controls. Even if an attacker gains access to a less sensitive segment, they would not automatically have access to sensitive or mission-critical data.
3. Reducing the Attack Surface
By limiting communication between network segments, network segmentation reduces the overall attack surface. Attackers cannot easily traverse the network to exploit vulnerabilities in different systems. Each segment is secured with specific policies, firewalls, and monitoring tools that make it more difficult for attackers to exploit weaknesses within the network.
4. Implementing Zero Trust Architecture
Network segmentation is an essential component of Zero Trust Architecture (ZTA), which assumes that no entity, inside or outside the network, should be trusted by default. With ZTA, every user, device, and application must be authenticated and authorized to access resources. By isolating network segments, an organization can enforce more granular access controls and continuously verify the identity of users and devices attempting to access sensitive resources.
5. Monitoring and Detection
With network segmentation, it becomes easier to detect anomalous activity within specific segments. Security tools can focus their monitoring efforts on isolated network segments, looking for unusual behavior that may indicate a lateral attack. By narrowing down the scope of monitoring, security teams can more effectively identify and respond to threats before they spread throughout the entire network.
Key Components of Effective Network Segmentation
For network segmentation to be effective in preventing lateral attacks, it must be implemented thoughtfully and strategically. Here are the key components of effective segmentation:
1. Clear Definition of Network Zones
The first step in network segmentation is to define clear zones or segments based on factors such as function, sensitivity, and risk level. For example, organizations may have separate segments for:
- Public-facing servers (e.g., web servers, email servers)
- Internal employee networks
- Sensitive databases and file systems
- Operational technology (OT) or industrial control systems (ICS)
- Guest networks or IoT devices
Each of these zones should have tailored security policies and access controls to ensure that the network is properly isolated.
2. Strong Access Controls and Authentication
Implementing robust access control mechanisms is essential to ensure that only authorized users can access specific segments. This can include multi-factor authentication (MFA), role-based access control (RBAC), and least privilege access policies. Ensuring that users only have access to the specific segments they need to perform their jobs is key to preventing lateral movement.
3. Micro-Segmentation
Micro-segmentation is a more granular approach to network segmentation, where individual workloads or applications are isolated within the network. It involves segmenting the network down to smaller units, such as virtual machines, containers, or even specific services within an application. Micro-segmentation provides tighter control over traffic flow and enhances security by creating more finely-tuned security boundaries.
4. Use of Firewalls and Virtual Local Area Networks (VLANs)
Firewalls and VLANs are commonly used to enforce segmentation. Firewalls can be configured to monitor and control traffic between network segments, ensuring that only authorized traffic is allowed to pass through. VLANs, on the other hand, logically separate networks within a single physical infrastructure, ensuring that each segment operates independently, even if they share the same hardware.
5. Ongoing Network Monitoring and Threat Detection
Once segmentation is in place, continuous monitoring is necessary to detect potential threats within each segment. Intrusion Detection Systems (IDS) and Security Information and Event Management (SIEM) tools can be used to monitor traffic within segments and provide alerts when suspicious behavior is detected. Behavioral analytics and anomaly detection can help identify lateral movements or reconnaissance activities, even in segmented parts of the network.
Challenges in Implementing Network Segmentation
While network segmentation offers significant advantages, its implementation is not without challenges. Some of the key hurdles include:
1. Complexity and Cost
Implementing network segmentation requires careful planning, additional hardware, and software investments. For larger organizations, it can be a complex and resource-intensive process to segment the network in a way that balances security with operational efficiency.
2. Potential for Misconfiguration
Incorrectly configured network segments can lead to security vulnerabilities. Misconfigured access controls or improperly segmented networks could inadvertently allow attackers to bypass the barriers and move laterally. Organizations need to ensure that segmentation is set up correctly from the beginning and continuously tested for vulnerabilities.
3. Maintaining Operational Efficiency
Network segmentation can sometimes hinder the free flow of data between different parts of the organization. Organizations need to ensure that segmentation does not disrupt business operations, particularly when legitimate data sharing or communication is required between different network segments.
Best Practices for Preventing Lateral Attacks with Network Segmentation
To maximize the effectiveness of network segmentation in preventing lateral attacks, organizations should adhere to the following best practices:
1. Conduct a Network Assessment
Before implementing segmentation, conduct a comprehensive network assessment to identify critical assets, data flows, and vulnerabilities. This will help determine the appropriate segmentation strategy and ensure that the most sensitive parts of the network are adequately protected.
2. Implement Segmentation Based on Risk
Segment the network based on the value and sensitivity of the data and systems in each zone. High-risk areas, such as customer data or intellectual property, should be isolated in separate segments, while less critical systems can be grouped together.
3. Apply Principle of Least Privilege
Enforce the principle of least privilege to ensure that users and devices only have access to the network segments they need to perform their functions. This minimizes the potential attack surface and reduces the ability of attackers to move laterally.
4. Regularly Test and Update Network Segmentation
Regularly test network segmentation configurations to identify any gaps or misconfigurations. Additionally, update segmentation strategies as the network evolves to accommodate new technologies, applications, or changes in business needs.
Conclusion
Network segmentation plays a crucial role in preventing lateral attacks by isolating critical systems and data, reducing the attack surface, and containing breaches to specific segments of the network. By implementing effective segmentation strategies, organizations can prevent attackers from easily moving within the network and accessing sensitive information. While the process of implementing segmentation can be complex, the benefits in terms of enhanced security and reduced risk of lateral attacks make it a fundamental component of a robust cybersecurity strategy.
Q&A Section
1. What is network segmentation?
Ans:- Network segmentation is the practice of dividing a larger network into smaller, isolated sub-networks or segments to improve security and performance.
2. How does network segmentation help prevent lateral attacks?
Ans:- By isolating sensitive data and systems into separate segments, attackers cannot easily move across the network if they breach one segment.
3. What are lateral attacks in cybersecurity?
Ans:- Lateral attacks occur when a hacker moves from one compromised system to another within the same network, often escalating privileges and gaining access to more valuable data.
4. Why are lateral attacks a major concern for businesses?
Ans:- Lateral attacks allow cybercriminals to freely access and exploit internal systems without needing to breach external defenses, making them harder to detect.
5. How does segmentation limit the impact of a breach?
Ans:- It confines the breach to a single segment, reducing the attacker's ability to access other parts of the network and preventing widespread damage.
6. What is the difference between network segmentation and network isolation?
Ans:- While both limit access to specific parts of the network, isolation refers to completely separating segments from each other, whereas segmentation can allow controlled communication between segments.
7. Can network segmentation prevent all types of lateral attacks?
Ans:- While it significantly reduces the risk, network segmentation is not foolproof. It should be combined with other security measures like strong authentication and intrusion detection.
8. How can businesses implement network segmentation?
Ans:- Businesses can use firewalls, virtual LANs (VLANs), and software-defined networking (SDN) to segment their networks based on function, sensitivity, and access control policies.
9. What are some best practices for effective network segmentation?
Ans:- Best practices include defining clear access control policies, limiting communication between segments, monitoring segment traffic, and regularly reviewing segmentation strategies.
10. How does network segmentation align with the Zero Trust model?
Ans:- Network segmentation supports the Zero Trust model by ensuring that even if an attacker gains access to one segment, they cannot move freely to other segments without authorization.
Similar Articles
Find more relatable content in similar Articles

Digital inclusion: designing d..
Designing technology for elder.. Read More

Digital Privacy in 2025: How S..
In 2025, digital privacy faces.. Read More

From Phishing to Data Theft: ..
Cybercrime in India is evolvi.. Read More

Cloud PCs: Will Your Next Comp..
Cloud PCs are transforming the.. Read More
Explore Other Categories
Explore many different categories of articles ranging from Gadgets to Security
Smart Devices, Gear & Innovations
Discover in-depth reviews, hands-on experiences, and expert insights on the newest gadgets—from smartphones to smartwatches, headphones, wearables, and everything in between. Stay ahead with the latest in tech gear
Apps That Power Your World
Explore essential mobile and desktop applications across all platforms. From productivity boosters to creative tools, we cover updates, recommendations, and how-tos to make your digital life easier and more efficient.
Tomorrow's Technology, Today's Insights
Dive into the world of emerging technologies, AI breakthroughs, space tech, robotics, and innovations shaping the future. Stay informed on what's next in the evolution of science and technology.
Protecting You in a Digital Age
Learn how to secure your data, protect your privacy, and understand the latest in online threats. We break down complex cybersecurity topics into practical advice for everyday users and professionals alike.
© 2025 Copyrights by rTechnology. All Rights Reserved.