
Cloud security challenges with multi-cloud setups
Multi-cloud setups offer flexibility and resilience but introduce complex security challenges. Issues such as inconsistent policies, misconfigurations, IAM gaps, data privacy, compliance, and third-party vulnerabilities increase risks. Effective security requires unified monitoring, strong encryption, centralized access control, and adherence to regulations.
✨ Raghav Jain
Introduction
As organizations increasingly adopt cloud computing, many are moving beyond a single cloud provider to a multi-cloud strategy. Multi-cloud setups—where a business uses multiple cloud services from different vendors—offer flexibility, cost optimization, and redundancy. However, they also introduce complex security challenges that can put sensitive data, applications, and systems at risk.
Understanding the security landscape of multi-cloud environments is critical for IT teams, security professionals, and businesses that want to maintain data integrity, compliance, and operational resilience. In this article, we explore the key cloud security challenges in multi-cloud setups, their causes, and practical strategies to mitigate risks. The adoption of cloud computing has become a strategic necessity for organizations of all sizes, driven by the need for agility, scalability, and cost efficiency. However, as businesses increasingly move beyond single cloud environments to embrace multi-cloud strategies, where services from multiple providers are used simultaneously, a new set of security challenges emerges. Multi-cloud setups offer significant benefits, such as avoiding vendor lock-in, enhancing redundancy, and optimizing workload performance. Yet, these advantages come at the cost of increased complexity in managing security across diverse platforms, each with its own policies, architectures, and tools.
One of the primary challenges in multi-cloud security is visibility. When an organization uses multiple cloud providers, it becomes difficult to maintain a comprehensive view of all assets, data flows, and potential vulnerabilities. Each provider typically offers its own monitoring and reporting tools, which may not be interoperable or standardized. This fragmentation makes it harder for security teams to detect anomalous behavior or potential breaches quickly. Without a unified visibility layer, organizations risk gaps in monitoring that attackers can exploit, making incident response slower and less effective.
Data security represents another significant challenge in multi-cloud environments. Companies must ensure that sensitive information is protected as it moves between different clouds and within each individual environment. Encryption becomes crucial, both at rest and in transit, yet implementing consistent encryption policies across multiple platforms is complex. Each cloud provider may have different encryption standards, key management practices, and access controls, which can result in misconfigurations or overlooked vulnerabilities. Furthermore, ensuring compliance with data protection regulations such as GDPR, HIPAA, or CCPA adds another layer of complexity, as data may traverse geographic boundaries and different legal jurisdictions, complicating governance and risk management.
Identity and access management (IAM) in multi-cloud setups is another area fraught with challenges. Managing user identities and permissions across multiple clouds requires careful coordination to prevent unauthorized access. Misconfigured IAM roles or inconsistent access policies can create vulnerabilities that attackers may exploit. Additionally, the proliferation of service accounts, API keys, and privileged accounts across different platforms increases the attack surface. Organizations must establish robust processes for authentication, authorization, and credential rotation while ensuring consistent enforcement across all cloud environments. Failing to do so can lead to privilege escalation attacks or unauthorized data exposure.
Network security is also significantly more complex in a multi-cloud architecture. Traffic may flow between clouds, on-premises environments, and end users, creating multiple points of vulnerability. Organizations need to implement secure connectivity mechanisms, such as VPNs, dedicated interconnects, or zero-trust network architectures, to protect data in transit. Segmentation of network resources becomes essential to limit lateral movement in case of a breach. However, implementing consistent network security policies across heterogeneous clouds is a demanding task, often requiring specialized knowledge of each provider’s tools and configurations.
Another pressing concern is the management of misconfigurations, which remain one of the leading causes of cloud security breaches. Each cloud provider has unique configuration settings, security defaults, and resource hierarchies. In a multi-cloud setup, ensuring that all resources are correctly configured according to best practices can be daunting. Misconfigurations such as overly permissive storage buckets, exposed management interfaces, or incorrect firewall rules can easily go unnoticed. The risk multiplies as organizations scale their cloud deployments, making automated security assessment tools and continuous monitoring indispensable.
The challenge of consistent policy enforcement is closely tied to these issues. Organizations must develop unified security policies that can be applied across all cloud platforms, yet the practical implementation often faces technical limitations. Native security tools from different providers may not support uniform policy definitions, requiring additional third-party solutions or custom automation scripts. Achieving policy consistency is critical not only for security but also for compliance audits and reporting. Without consistent policies, organizations may unknowingly introduce vulnerabilities, creating weak links that compromise the overall security posture.
Incident response and disaster recovery planning in multi-cloud environments also require careful attention. A security incident affecting one cloud provider could have cascading effects on applications or data hosted in another, especially if dependencies between platforms are not well understood. Organizations must design response plans that account for the complexities of multi-cloud operations, including coordination between providers, automated alerts, and predefined escalation procedures. Similarly, disaster recovery strategies must be adapted to ensure data integrity and availability across multiple clouds, accounting for potential differences in backup mechanisms, replication methods, and restoration times.
The human factor adds another layer of challenge to multi-cloud security. Managing diverse environments requires skilled personnel familiar with different cloud platforms, security frameworks, and regulatory requirements. Shortages of cloud security experts can lead to oversight, delayed response times, and errors in configuration or monitoring. Training and continuous upskilling are essential to keep pace with the rapidly evolving cloud landscape. Additionally, internal collaboration between development, operations, and security teams must be strengthened to ensure that security is integrated throughout the cloud lifecycle.
Finally, supply chain and third-party risks become more pronounced in a multi-cloud scenario. Organizations often rely on additional vendors, software solutions, and managed services within their cloud infrastructure. Each additional service introduces potential vulnerabilities, from weak security practices to compromised APIs or libraries. Coordinating risk management across multiple external entities requires rigorous vendor assessment, contract stipulations, and ongoing monitoring to mitigate exposure.
In conclusion, while multi-cloud setups provide strategic benefits such as flexibility, redundancy, and cost optimization, they introduce significant security challenges that must be addressed proactively. Organizations must invest in comprehensive visibility tools, robust identity and access management, consistent encryption, unified policy enforcement, and skilled personnel. Continuous monitoring, automated misconfiguration detection, and well-defined incident response plans are critical to maintaining a strong security posture. By recognizing and systematically addressing the complexities inherent in multi-cloud environments, businesses can harness the advantages of multi-cloud architectures while mitigating the risks associated with dispersed and heterogeneous infrastructures. Effective multi-cloud security requires not just technology but also processes, governance, and people working in harmony to protect sensitive data and maintain operational resilience in an increasingly interconnected digital landscape.
What is Multi-Cloud Security?
Multi-cloud security refers to the set of policies, tools, and practices that protect data, applications, and workloads distributed across two or more cloud providers. Unlike single-cloud security, multi-cloud environments involve diverse architectures, APIs, and compliance frameworks, which increase complexity.
A secure multi-cloud environment ensures:
- Data confidentiality – sensitive information is encrypted and protected
- Data integrity – data remains accurate and uncorrupted
- Availability – services remain accessible even in the event of failures
- Compliance adherence – meeting industry standards like GDPR, HIPAA, or ISO 27001
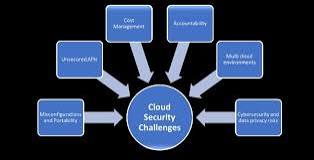
Common Challenges in Multi-Cloud Security
1. Complex Access Management
With multiple providers, managing user access across various systems becomes difficult. Risks include:
- Overprivileged accounts
- Uncoordinated identity management
- Unauthorized access across platforms
Solution: Implement centralized identity and access management (IAM) systems, enforce multi-factor authentication, and regularly audit user permissions.
2. Data Protection and Compliance Issues
Different clouds may store data in various locations, sometimes across countries. This can create:
- Data residency compliance issues
- Inconsistent encryption practices
- Difficulty tracking where sensitive data resides
Solution: Use data classification, encrypt data in transit and at rest, and maintain a compliance mapping strategy across all clouds.
3. Visibility Gaps
Monitoring multiple clouds can lead to blind spots where malicious activity goes undetected. Security teams may struggle to:
- Identify anomalous activity
- Track configuration changes
- Consolidate logs from multiple providers
Solution: Implement unified cloud monitoring and security information event management (SIEM) tools that aggregate data from all cloud environments.
4. Configuration Errors and Mismanagement
Misconfigured cloud services are a leading cause of breaches. Multi-cloud setups increase the chances of:
- Publicly exposed storage buckets
- Weak firewall rules
- Mismanaged API permissions
Solution: Automate configuration checks using cloud security posture management (CSPM) tools and enforce security best practices consistently across providers.
5. Network Security Complexity
Multi-cloud networks often involve complex architectures with VPNs, direct connects, and hybrid links. Challenges include:
- Securing inter-cloud traffic
- Protecting against lateral movement of threats
- Maintaining segmentation between different workloads
Solution: Adopt zero-trust networking principles, encrypt inter-cloud communication, and define strict segmentation policies.
6. Third-Party Risks
Each cloud provider may rely on its own vendors and third-party integrations. Risks include:
- Vulnerabilities in vendor software
- Supply chain attacks
- Inconsistent patch management
Solution: Evaluate third-party security regularly, enforce contractual security obligations, and monitor software updates and patches.
7. Incident Response and Recovery Challenges
Coordinating a security response across multiple clouds is difficult because:
- Logs and alerts are in different formats
- Response procedures vary by provider
- Recovery timelines may not be aligned
Solution: Create a unified incident response plan, train staff for multi-cloud incidents, and regularly test disaster recovery scenarios.
Daily and Weekly Practices to Secure Multi-Cloud Environments
Daily Practices:
- Monitor cloud logs for unusual activity
- Review user access and revoke unnecessary privileges
- Apply critical patches and updates
- Scan for misconfigured storage, databases, and APIs
Weekly Practices:
- Audit compliance with industry standards
- Test incident response playbooks
- Validate backups and disaster recovery plans
- Rotate encryption keys and credentials if needed
Best Practices for Multi-Cloud Security
- Centralized Security Policies
- Develop unified policies that cover all cloud providers to avoid inconsistencies.
- Automation and AI-Powered Security
- Use tools that automatically detect misconfigurations, suspicious behavior, and vulnerabilities.
- Zero-Trust Approach
- Never assume any cloud workload is safe by default. Authenticate and verify every access attempt.
- Strong Encryption Standards
- Encrypt data both in transit and at rest, using provider-independent keys if possible.
- Regular Training
- Educate IT and security teams on the differences between cloud platforms and emerging threats.
- Vendor Risk Management
- Evaluate third-party dependencies and ensure they follow strict security practices.
Common Myths About Multi-Cloud Security: Busted!
“Using multiple clouds automatically increases security.”
→ False. Complexity often introduces more vulnerabilities rather than reducing them.
“Cloud providers are fully responsible for security.”
→ Wrong. Security is a shared responsibility: providers secure the infrastructure, but users are responsible for applications, data, and access.
“Firewalls alone are enough to secure multi-cloud setups.”
→ Incorrect. Firewalls are part of a layered approach; monitoring, encryption, and access management are equally essential.
“Compliance with one cloud provider ensures full regulatory adherence.”
→ False. Each provider may have different compliance coverage; organizations must ensure compliance across all clouds.
Sample Multi-Cloud Security Routine for Organizations
Morning Checks:
- Review alerts from SIEM dashboards
- Verify critical updates are applied
- Check access logs for anomalies
Afternoon Actions:
- Conduct configuration audits
- Rotate temporary credentials or keys
- Validate encrypted storage and backups
Evening / Weekly Practices:
- Test incident response procedures
- Review third-party vendor security updates
- Consolidate logs for cross-cloud analysis
Ongoing Practices:
- Automate compliance checks
- Train employees on cloud security awareness
- Perform vulnerability assessments across all platforms
Conclusion
Multi-cloud setups offer tremendous benefits in flexibility, performance, and redundancy. However, they also introduce significant security challenges—from access management and data protection to incident response and network security. Addressing these challenges requires centralized policies, automation, vigilance, and staff training.
By implementing consistent security practices, leveraging monitoring tools, and following best practices for encryption and access, organizations can minimize risks while reaping the advantages of multi-cloud environments.
Whether you’re a business leader, IT professional, or cloud engineer, understanding these challenges and applying proactive measures ensures your multi-cloud strategy is both innovative and secure.
Q&A Section
Q1:- What is a multi-cloud setup and why are companies adopting it?
Ans :- A multi-cloud setup involves using services from multiple cloud providers simultaneously to improve redundancy, flexibility, and avoid vendor lock-in. Companies adopt it to optimize costs, enhance performance, and ensure business continuity.
Q2:- What are the main security challenges in multi-cloud environments?
Ans :- Challenges include inconsistent security policies across providers, increased attack surfaces, misconfigurations, identity and access management issues, and difficulty in monitoring and auditing multiple platforms.
Q3:- How does data privacy become complicated in multi-cloud setups?
Ans :- Data often moves across different providers and regions, raising compliance challenges with laws like GDPR, HIPAA, and other regional regulations, making consistent data privacy enforcement difficult.
Q4:- Why are misconfigurations a major threat in multi-cloud security?
Ans :- Misconfigured storage buckets, virtual networks, or access controls can expose sensitive data to unauthorized access, making them one of the leading causes of cloud breaches.
Q5:- How does identity and access management (IAM) affect multi-cloud security?
Ans :- Poor IAM can lead to excessive privileges, weak authentication, and lack of centralized control, increasing the risk of unauthorized access across multiple cloud environments.
Q6:- What role does visibility and monitoring play in multi-cloud security?
Ans :- Without centralized monitoring, detecting threats, anomalies, or breaches becomes difficult. Security teams need unified dashboards and real-time alerts to manage risks effectively.
Q7:- How do compliance requirements complicate multi-cloud setups?
Ans :- Each cloud provider may have different compliance certifications and reporting standards. Companies must ensure that data handling meets regulatory requirements across all platforms.
Q8:- Why is data encryption critical in multi-cloud environments?
Ans :- Encrypting data in transit and at rest ensures confidentiality and integrity. Without strong encryption practices, sensitive information could be exposed during transfers between clouds.
Q9:- How do third-party integrations introduce vulnerabilities in multi-cloud systems?
Ans :- External tools and APIs can become weak points if not properly secured, potentially allowing attackers to exploit them to access multiple cloud services.
Q10:- What strategies can organizations adopt to strengthen multi-cloud security?
Ans :- Implement unified security policies, automated monitoring, robust IAM, encryption, regular audits, and choose cloud providers with strong compliance standards. Adopting a zero-trust model also enhances protection.
Similar Articles
Find more relatable content in similar Articles

Digital inclusion: designing d..
Designing technology for elder.. Read More

Post-quantum blockchains: desi..
Post-quantum blockchains explo.. Read More

Cloud PCs: Will Your Next Comp..
Cloud PCs are transforming the.. Read More

The Alarming Rise of Cybercrim..
Cybercrime in India is rising.. Read More
Explore Other Categories
Explore many different categories of articles ranging from Gadgets to Security
Smart Devices, Gear & Innovations
Discover in-depth reviews, hands-on experiences, and expert insights on the newest gadgets—from smartphones to smartwatches, headphones, wearables, and everything in between. Stay ahead with the latest in tech gear
Apps That Power Your World
Explore essential mobile and desktop applications across all platforms. From productivity boosters to creative tools, we cover updates, recommendations, and how-tos to make your digital life easier and more efficient.
Tomorrow's Technology, Today's Insights
Dive into the world of emerging technologies, AI breakthroughs, space tech, robotics, and innovations shaping the future. Stay informed on what's next in the evolution of science and technology.
Protecting You in a Digital Age
Learn how to secure your data, protect your privacy, and understand the latest in online threats. We break down complex cybersecurity topics into practical advice for everyday users and professionals alike.
© 2025 Copyrights by rTechnology. All Rights Reserved.