
How to Avoid Falling for Online Scams and Phishing.
With the rise of digital interactions, online scams, especially phishing attacks, have become more sophisticated and prevalent. Cybercriminals employ tactics like creating urgency, impersonating trusted entities, and exploiting human behavior to steal sensitive data. This guide explores various types of phishing attacks, offers actionable tips to spot scams, and outlines strategies like awareness, multi-factor authentication, and secure browsing to protect your information and online presence.
✨ Raghav Jain
How to Avoid Falling for Online Scams and Phishing
In today’s digital age, the internet has opened up countless opportunities for communication, entertainment, education, and commerce. However, this vast, interconnected network has also provided fertile ground for malicious actors seeking to exploit unsuspecting users. One of the most common threats online is scams, particularly phishing attacks. These scams can take many forms, and their deceptive nature can make them difficult to identify. Understanding how to avoid falling victim to online scams and phishing is essential for protecting personal information, finances, and overall online security. This article will explore common online scams, phishing techniques, and provide actionable steps to recognize, prevent, and protect yourself from such threats.
What are Online Scams and Phishing?
Online scams refer to deceptive practices designed to trick individuals into disclosing sensitive personal information, such as passwords, credit card numbers, or Social Security numbers. These scams can occur through various channels, including emails, websites, social media, and even phone calls. Phishing is a specific type of scam that typically involves fake communication that appears to be from a legitimate source, such as a bank, social media platform, or e-commerce site.
Phishing attacks often take the form of emails, instant messages, or social media posts that look legitimate but contain links to fraudulent websites. These fraudulent websites are designed to steal sensitive information by luring users to enter their personal details. Scammers often rely on psychological manipulation, creating a sense of urgency or fear to prompt victims into taking immediate action without thinking critically about the request.
Common Types of Online Scams
- Phishing Emails
- Phishing emails are one of the most prevalent types of online scams. They often appear to come from well-known organizations such as banks, e-commerce websites, or tech companies. These emails typically contain urgent messages, such as claiming your account has been compromised or offering a limited-time deal, and they direct you to a website that looks like the real thing but is designed to steal your information.
- Fake Tech Support Scams
- In these scams, the fraudster impersonates a tech support agent from companies like Microsoft or Apple. They will call or email you, claiming that your device is infected with malware or has a technical issue. The scammer will then offer to fix the problem remotely by gaining access to your computer, which can lead to the installation of malicious software or theft of personal information.
- Online Shopping Scams
- With the rise of e-commerce, online shopping scams have become widespread. Scammers set up fake online stores or auction sites, offering products at extremely low prices to entice consumers. Once the victim makes a purchase, they either receive nothing or a counterfeit item. These scams can also involve fraudulent payment systems that steal credit card information.
- Lottery and Prize Scams
- Victims of lottery scams receive an unsolicited email or message telling them they have won a large sum of money, a prize, or a luxury item. To claim the prize, the victim is asked to pay taxes or fees upfront, or they may be instructed to provide personal banking information. Once the money is sent, the victim often never hears from the scammer again.
- Social Media Scams
- Social media platforms are rife with scams, such as fake giveaways, fraudulent fundraisers, and phishing links. Scammers often create fake profiles to impersonate celebrities, companies, or influencers and trick users into donating money or sharing personal details. They may also use social engineering tactics to gain the trust of a person before executing their scam.
- Investment Scams
- Investment scams promise high returns with little risk. These scams can range from fake cryptocurrency investments to Ponzi schemes. Scammers often use sophisticated tactics to convince victims to invest large sums of money, only for the scammer to disappear with the funds once the victim has paid.
How to Identify Phishing Attempts
Phishing attacks are sophisticated and can be difficult to detect. However, there are several signs to look out for:
- Suspicious Email Addresses or URLs
- Always check the sender’s email address or the URL of a website before clicking any links. Phishing emails often come from addresses that look similar to legitimate ones but contain subtle differences (e.g., misspelled domain names). Similarly, phishing websites may use URLs that appear similar to the real website but contain small variations, like extra characters or different domain extensions.
- Urgent or Threatening Language
- Phishing emails often create a sense of urgency, telling you to act quickly or risk losing access to your account. They may use phrases like “Immediate Action Required” or “Your Account Will Be Locked.” This tactic pressures you into making decisions without carefully considering the consequences.
- Poor Grammar and Spelling
- Legitimate organizations tend to have professional communication standards. If an email or message is filled with spelling errors, awkward phrasing, or unusual formatting, it is likely a phishing attempt.
- Suspicious Attachments or Links
- Phishing emails may contain attachments or links that, when clicked, take you to fraudulent websites or download malware to your computer. Never open attachments or click on links in unsolicited emails, especially if they seem irrelevant or unfamiliar.
- Unsolicited Requests for Sensitive Information
- Be wary of emails or messages that request personal information, such as passwords, credit card numbers, or Social Security numbers. Reputable organizations will never ask you to provide sensitive information via email or text.
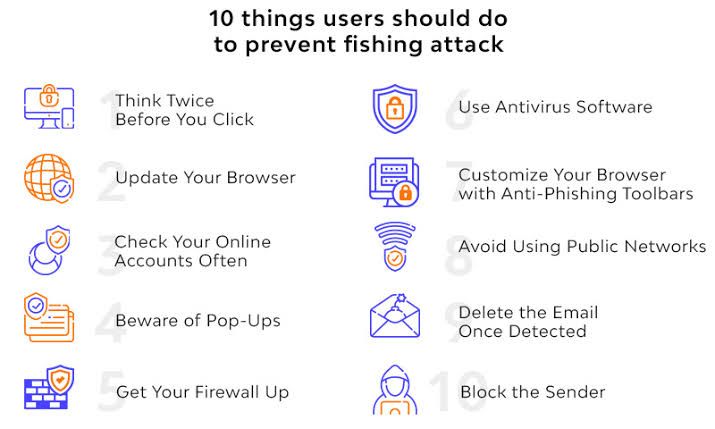
Steps to Protect Yourself from Online Scams and Phishing
- Use Strong and Unique Passwords
- Ensure your passwords are strong, long, and unique for each account. Consider using a password manager to securely store your passwords and generate complex ones. Avoid using common phrases or easily guessable information, such as birthdays or pet names.
- Enable Two-Factor Authentication (2FA)
- Enable two-factor authentication on your accounts whenever possible. This adds an extra layer of security by requiring you to enter a code sent to your phone or email in addition to your password. Even if a scammer obtains your password, they won’t be able to access your account without the second factor.
- Be Skeptical of Unsolicited Communication
- Always be cautious when receiving unsolicited emails, messages, or phone calls. Even if the sender seems legitimate, double-check by contacting the company or individual through a verified method (e.g., their official website or customer support number).
- Keep Your Software and Antivirus Programs Updated
- Regularly update your operating system, web browsers, and antivirus software. Updates often contain security patches that help protect against new types of online threats. Ensure your antivirus program is running in the background and regularly scanning your system for malicious software.
- Educate Yourself and Others
- Stay informed about the latest online scams and phishing techniques. Awareness is one of the most powerful tools in preventing cybercrime. Share this knowledge with friends and family, particularly older individuals who may be more susceptible to scams.
- Verify Website Security
- Before entering sensitive information on a website, check that the site is secure. Look for a padlock symbol next to the URL in your browser or ensure the URL starts with “https://” rather than just “http://”. While this doesn’t guarantee the site is legitimate, it does help ensure your data is encrypted.
- Report Suspicious Activity
- If you receive a suspicious email, text, or phone call, report it to the relevant authorities or companies. Most financial institutions, e-commerce websites, and social media platforms have mechanisms for reporting phishing attempts and scams. Reporting helps prevent others from falling victim.
The digital age has brought immense convenience to our lives, but it has also ushered in a host of new threats, particularly online scams and phishing attacks, which have become a ubiquitous and evolving menace on the internet. These scams, which range from fake job offers to fraudulent e-commerce websites, exploit human psychology, and prey on trust, urgency, and fear, making them particularly effective. Phishing, a type of cyber attack, has become a significant method for cybercriminals to gain access to sensitive information such as passwords, financial data, and even social security numbers. Often disguised as legitimate communications from well-known entities like banks, social media platforms, or government agencies, phishing emails and messages may contain links or attachments that, when clicked, redirect users to fraudulent websites or install malware on their devices. One of the most alarming aspects of these attacks is their ability to blend seamlessly into legitimate communication, making it difficult for even experienced users to spot them. Scammers often use sophisticated tactics such as mimicking the visual design of trusted websites, using email addresses that closely resemble official domains, and creating a sense of urgency, such as claiming that an account has been compromised or a limited-time offer is about to expire. These attacks exploit the trust that users have in recognizable brands or institutions, which is why it’s essential to adopt a vigilant and skeptical approach to any unsolicited communication. One common characteristic of phishing attacks is the use of threatening or urgent language, which pressures the recipient into making quick decisions without thoroughly analyzing the situation. This tactic works because it capitalizes on the human tendency to act quickly in the face of fear or perceived danger. For instance, a scammer may send an email that claims, "Your account will be locked unless you verify your details immediately," pushing the victim into clicking on a fraudulent link that appears to be from a bank or an online service. Unfortunately, once the victim provides the requested details, the scammer has access to critical personal information, which may lead to financial loss or identity theft. Another technique used in phishing is the creation of fake websites that closely resemble real, trusted platforms. These websites often feature identical logos, branding, and even URLs that are nearly indistinguishable from legitimate sites. Users, without noticing the subtle differences in spelling or domain extension, may unwittingly enter their personal information, which is then stolen by cybercriminals. Additionally, phishing can occur over text messages (SMS phishing or smishing) and social media platforms, where attackers try to establish a rapport with potential victims before convincing them to click on malicious links or share sensitive data. It's also worth noting that phishing isn't always about stealing information directly. In some cases, it is a precursor to more elaborate scams, such as ransomware attacks, where the attacker gains access to the victim’s system, encrypts their files, and demands payment for the decryption key. One of the most important steps to preventing falling victim to phishing scams is awareness. Regularly educating oneself about common phishing tactics can go a long way in recognizing potential threats. A key preventative measure is to always verify the source of any unsolicited communication, particularly if it requests personal or financial information. Instead of responding to the email or message directly, it’s advisable to contact the company or individual using contact information found on their official website or through trusted sources. Another way to guard against phishing attacks is by paying close attention to the finer details of any message or website. Suspicious signs include generic greetings, poor grammar, broken links, or mismatched URL domains. Furthermore, enabling two-factor authentication (2FA) adds an additional layer of security to your online accounts. Even if a hacker obtains your password through phishing, they would still need access to a second factor, such as a phone number or authentication app, to gain entry. Regularly updating your passwords and using strong, unique combinations for different accounts can further reduce the risk of falling victim to scams. Moreover, utilizing security software and firewalls can help detect and block malicious websites or malware, adding another layer of protection against cyber threats. Despite these preventative measures, there’s no foolproof method for avoiding scams entirely, as cybercriminals are continuously adapting their strategies. As such, maintaining a healthy skepticism toward unsolicited communication and avoiding sharing sensitive personal information via email or text is crucial. Furthermore, it’s essential to act quickly if you suspect you’ve fallen victim to a phishing attack. Immediately changing passwords, notifying financial institutions, and reporting the incident to relevant authorities can help mitigate any potential damage. While the internet provides endless opportunities for social connection, business, and entertainment, it’s also a space where malicious actors lurk, seeking to exploit vulnerabilities in human behavior. Thus, the responsibility to protect oneself from online scams and phishing attacks lies with the individual. By staying vigilant, educating oneself about the latest cyber threats, and using a combination of technical defenses such as 2FA and antivirus software, we can reduce the chances of falling victim to these attacks and enjoy a safer online experience. Ultimately, the more we understand how scams work and the tactics employed by cybercriminals, the better equipped we become to recognize and avoid these malicious activities.
The rapid expansion of the internet and the increasing reliance on digital platforms for communication, shopping, banking, and social interaction have inevitably created a parallel rise in online threats, most notably scams and phishing attacks, which have evolved in complexity and sophistication over the years, posing significant risks to individuals and organizations alike. Scams, in the context of the internet, refer to fraudulent schemes aimed at deceiving individuals to steal their money, personal data, or other sensitive information. One of the most common forms of online scam is phishing, a cybercrime tactic where attackers impersonate legitimate entities, such as banks, e-commerce websites, or government organizations, to trick victims into providing confidential information, including passwords, credit card details, or social security numbers. These phishing attempts typically come in the form of emails, text messages, or pop-up ads that appear to be from reputable sources. The goal is to exploit the victim’s trust and the sense of urgency the attacker creates, encouraging them to click on malicious links, download attachments, or provide personal data without carefully scrutinizing the request. While phishing is a widely recognized threat, the tactics employed by cybercriminals have become increasingly sophisticated, often involving highly professional-looking communications that are designed to mimic real interactions. The messages often feature logos, formatting, and writing styles that appear to come from well-known organizations, making it difficult for users to distinguish legitimate messages from malicious ones. This creates a dangerous environment for individuals who are not well-versed in identifying phishing attempts, especially considering how these scams are often executed through familiar channels such as email, SMS (text messages), and social media platforms, which many people use daily for both personal and professional purposes. One of the primary psychological strategies employed in phishing is the use of urgency and fear. Phishers know that humans are naturally inclined to act quickly when faced with a perceived threat, which is why phishing messages often include alarming statements like "Your account has been compromised" or "Immediate action required to avoid suspension." These statements trigger an emotional reaction in the recipient, causing them to act impulsively and without considering the consequences of clicking on a suspicious link or entering their sensitive information. For example, a phishing email may claim that an account has been locked and instruct the recipient to click a link to unlock it, only to direct them to a fraudulent website designed to capture login credentials. This sense of urgency can cloud judgment, making it much more likely for individuals to fall victim to these scams. Furthermore, cybercriminals often use techniques such as social engineering to build rapport and gain the victim’s trust. For instance, scammers might impersonate customer support representatives from companies that the victim already does business with, providing a false sense of familiarity and legitimacy. Another increasingly common phishing method is spear-phishing, where attackers target specific individuals or organizations by gathering personal information to make their attack more convincing. This could involve using publicly available data from social media profiles, data breaches, or other sources to craft a message that is highly personalized, making it even more difficult to detect. The attack may even be aimed at employees of a particular company, where the attacker poses as a colleague or boss in order to steal sensitive corporate information or gain access to company accounts. As phishing techniques continue to grow more sophisticated, the threat of falling victim to such scams becomes more prominent. However, there are several steps individuals can take to protect themselves from falling prey to these types of attacks. The first and foremost defense against phishing is awareness. It is essential for internet users to understand the warning signs of phishing emails and other scams. A major red flag is any unsolicited message requesting sensitive information, especially if the request is urgent or comes from an unfamiliar sender. Furthermore, phishing emails may often include spelling or grammatical errors, which are not typical of legitimate communications from reputable companies. Another sign of a phishing attempt is generic language, such as addressing the recipient with impersonal terms like "Dear Customer" rather than using their name. Phishers often target people in bulk, so using generic language is a tactic to avoid personalization. Also, recipients should be wary of any unexpected attachments or links in emails, as phishing attacks commonly rely on malicious URLs that lead to fraudulent websites. It is always advisable to hover over links before clicking on them to check the actual URL to ensure it matches the official website of the organization it claims to be from. One of the most effective ways to protect yourself from phishing attacks is by using multi-factor authentication (MFA) wherever possible. MFA adds an additional layer of security to your accounts by requiring a second form of verification, such as a one-time passcode sent to your phone, in addition to your usual password. Even if a phisher manages to obtain your password, they will still need access to the second factor to gain entry into your account. This significantly reduces the chances of an attacker successfully infiltrating your online accounts. Another key defensive measure is to keep your software, web browsers, and antivirus programs up to date. Many cyberattacks, including phishing, exploit vulnerabilities in outdated software. By regularly updating your devices and using reputable security software, you can reduce the risk of malware infections and phishing attacks. In addition to technical measures, maintaining a cautious and skeptical attitude when interacting with unsolicited communications is critical. Whenever you receive an email, text message, or phone call that requests sensitive information, it is essential to take the time to verify the legitimacy of the request. Instead of clicking on links or replying to the message directly, contact the organization or individual using official contact details from their website or other trusted sources. This simple step can help you avoid falling for phishing scams. Moreover, practicing good password hygiene is another way to safeguard against phishing attacks. Using strong, unique passwords for each of your accounts ensures that even if one account is compromised, others remain secure. Password managers can help store and generate strong passwords, making it easier to manage your online security. For organizations, educating employees about phishing attacks and conducting regular security awareness training is crucial in preventing corporate-level cybercrimes. Employees should be taught how to recognize phishing attempts, how to verify suspicious requests, and how to report phishing emails to the appropriate IT department. Finally, always be aware of your digital footprint. Phishing attacks are often more effective when attackers have access to personal information that they can use to craft convincing messages. Being mindful of the personal information you share online, especially on social media, can help minimize the chances of an attacker using that data to create a personalized phishing attack. In the world of online security, where threats are constantly evolving, the key to protecting yourself from phishing scams is a combination of vigilance, skepticism, and utilizing the latest security measures. By staying informed about the latest phishing tactics, adopting a proactive approach to online security, and implementing both technical and psychological defenses, individuals and organizations can reduce the likelihood of falling victim to scams and phishing attacks. While the internet offers endless opportunities for convenience and connectivity, it’s crucial to remember that with these opportunities come significant risks, and only by remaining alert and cautious can we truly safeguard our personal and professional information from malicious actors lurking in the digital realm.
Conclusion
In an era where digital interactions are a regular part of our daily lives, protecting ourselves from online scams and phishing is more important than ever. Scammers are constantly evolving their tactics, making it challenging to stay one step ahead. However, by staying vigilant, educating yourself on common scams, and implementing strong security practices, you can significantly reduce the risk of falling victim to these malicious attacks.
The key to avoiding online scams and phishing is awareness. Understanding the signs of phishing, adopting good security habits, and remaining skeptical of unsolicited communication are all effective ways to protect yourself. Additionally, the use of strong passwords, two-factor authentication, and regular software updates will help keep your online activities secure.
By taking these preventive measures, you can continue to enjoy the benefits of the internet while safeguarding your personal information and privacy.
Q&A Section
Q1: What is phishing, and how does it differ from other online scams?
Ans: Phishing is a type of online scam where scammers impersonate legitimate organizations to trick individuals into revealing sensitive information. Unlike other scams, phishing often involves fraudulent emails or websites that look genuine, but are designed to steal personal details like passwords and credit card numbers.
Q2: How can I identify a phishing email?
Ans: Phishing emails often have suspicious email addresses, contain urgent or threatening language, have poor grammar and spelling, and ask for sensitive information. Additionally, they may include attachments or links that lead to fraudulent websites. Always verify the sender’s email and double-check links before clicking.
Q3: What are some common types of online scams?
Ans: Common online scams include phishing emails, fake tech support scams, online shopping scams, lottery and prize scams, social media scams, and investment scams. Each of these scams employs different tactics to deceive individuals into revealing personal information or sending money.
Q4: How can I protect myself from online scams and phishing?
Ans: To protect yourself, use strong, unique passwords, enable two-factor authentication, be cautious of unsolicited communication, and keep your software and antivirus programs updated. Additionally, educate yourself about current scams, verify website security, and report suspicious activity.
Q5: What should I do if I fall victim to an online scam or phishing attack?
Ans: If you suspect you’ve been scammed, immediately change your passwords, contact your bank or credit card company, and report the scam to relevant authorities or the organization the scammer impersonated. If necessary, file a report with your local law enforcement or cybercrime agencies.
Similar Articles
Find more relatable content in similar Articles

3D-Printed Organs: Are We Clos..
3D-printed organs are at the f.. Read More

The Future of Electric Planes ..
The aviation industry is under.. Read More

Virtual Reality Therapy: Heali..
Virtual Reality Therapy (VRT) .. Read More

E-Waste Crisis: The Race to Bu..
The rapid growth of electronic.. Read More
Explore Other Categories
Explore many different categories of articles ranging from Gadgets to Security
Smart Devices, Gear & Innovations
Discover in-depth reviews, hands-on experiences, and expert insights on the newest gadgets—from smartphones to smartwatches, headphones, wearables, and everything in between. Stay ahead with the latest in tech gear
Apps That Power Your World
Explore essential mobile and desktop applications across all platforms. From productivity boosters to creative tools, we cover updates, recommendations, and how-tos to make your digital life easier and more efficient.
Tomorrow's Technology, Today's Insights
Dive into the world of emerging technologies, AI breakthroughs, space tech, robotics, and innovations shaping the future. Stay informed on what's next in the evolution of science and technology.
Protecting You in a Digital Age
Learn how to secure your data, protect your privacy, and understand the latest in online threats. We break down complex cybersecurity topics into practical advice for everyday users and professionals alike.
© 2025 Copyrights by rTechnology. All Rights Reserved.