
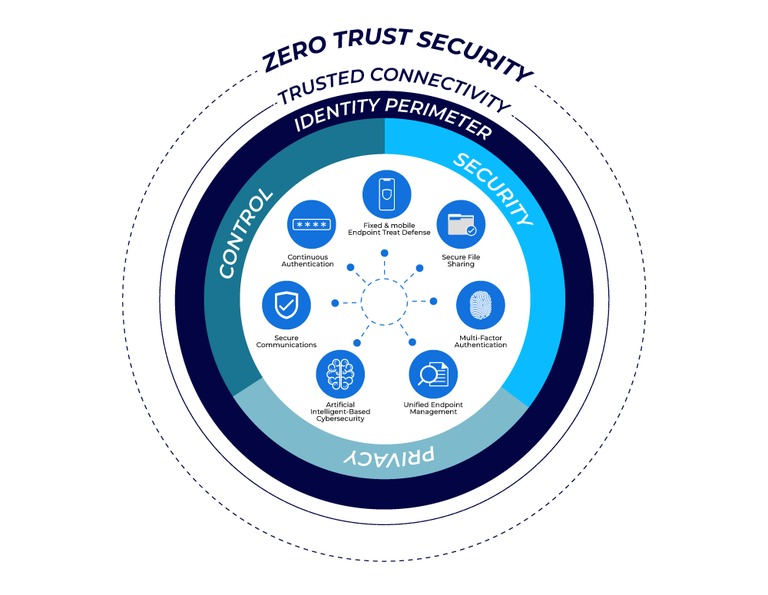
Zero trust security in IoT networks.
As IoT devices proliferate across homes, industries, and cities, traditional security models fail to address the growing threats from cyberattacks, data breaches, and unauthorized access. Zero Trust Security offers a revolutionary approach by continuously verifying every device, user, and connection, enforcing least privilege access, and leveraging AI-driven monitoring, ensuring resilient, adaptive, and secure IoT networks in an increasingly hyperconnected world.
✨ Raghav Jain
Introduction
The Internet of Things (IoT) has revolutionized the way we interact with technology. From smart homes and connected cars to industrial sensors and healthcare wearables, IoT devices now number in the tens of billions. However, this interconnected web also expands the attack surface exponentially. Each device, often with minimal security controls, becomes a potential entry point for cybercriminals. Traditional network security models—based on trust within a defined perimeter—are no longer sufficient in this decentralized and dynamic environment.
This is where Zero Trust Security (ZTS) emerges as a transformative paradigm. Rooted in the principle of “never trust, always verify,” Zero Trust shifts the focus from perimeter defense to continuous authentication, authorization, and monitoring of every device, user, and data flow—regardless of origin. For IoT networks, where diversity, scale, and heterogeneity dominate, Zero Trust offers a systematic framework for mitigating risks while ensuring scalability, resilience, and privacy.
1. The Rise of IoT and Its Security Challenges
IoT networks have expanded rapidly, encompassing devices across homes, industries, agriculture, healthcare, transportation, and even smart cities. Gartner predicts there will be more than 30 billion connected IoT devices by 2030, each collecting and transmitting vast amounts of data. While this connectivity drives innovation, it also introduces serious vulnerabilities.
Common IoT Security Challenges:
- Device Diversity: IoT ecosystems comprise devices with varied operating systems, capabilities, and firmware—making uniform security implementation difficult.
- Weak Authentication: Many IoT devices lack robust authentication mechanisms or use default credentials, leaving them exposed.
- Unpatched Firmware: Limited update capabilities often mean vulnerabilities remain unaddressed.
- Resource Constraints: Low-power IoT devices lack the computational strength for advanced encryption or real-time threat detection.
- Distributed Architecture: With data and devices scattered across networks, cloud, and edge, maintaining centralized control is complex.
The 2016 Mirai botnet attack, which hijacked thousands of IoT devices to cripple major websites, remains a stark reminder of the potential impact of insecure IoT infrastructures. As such incidents multiply, the necessity of Zero Trust principles becomes clearer.
2. Understanding Zero Trust Security
Zero Trust Security is not a single technology but a security philosophy and architecture built around the idea that no device, user, or system should be inherently trusted—inside or outside the network perimeter. Developed initially by Forrester analyst John Kindervag, the Zero Trust model dismantles the notion of a trusted internal network.
Core Principles of Zero Trust:
- Verify Explicitly: Every access request must be authenticated and authorized using all available data points, including user identity, device health, location, and behavior.
- Least Privilege Access: Users and devices get only the minimum permissions necessary to perform their function.
- Assume Breach: Operate under the assumption that the network is already compromised; monitor continuously to detect anomalies and limit lateral movement.
Zero Trust represents a shift from implicit trust (traditional security) to continuous validation, which fits naturally with the fluid and borderless nature of IoT environments.
3. Applying Zero Trust to IoT Networks
Implementing Zero Trust in IoT networks requires adapting its principles to address the unique constraints and architectures of IoT ecosystems.
a. Device Identity and Authentication
Every IoT device must possess a unique cryptographic identity, similar to a digital passport. This identity can be validated through Public Key Infrastructure (PKI), hardware-based roots of trust, or blockchain-based identity management systems. By ensuring each device is authenticated before communication, Zero Trust eliminates rogue devices from the network.
b. Micro-Segmentation
Rather than treating all IoT devices as part of one trusted environment, Zero Trust divides the network into micro-segments—isolated zones with strict access controls. If one device or segment is compromised, the breach cannot spread laterally.
c. Continuous Monitoring and Analytics
IoT networks generate enormous telemetry data. Zero Trust frameworks use AI-driven analytics to continuously monitor device behavior, detect anomalies, and flag potential intrusions. For instance, if a smart thermostat suddenly attempts to access a security camera feed, it triggers an alert or automatic isolation.
d. Least Privilege and Access Control
Role-based access control (RBAC) and attribute-based access control (ABAC) limit each device or user’s access strictly to what they require. This minimizes the attack surface and prevents privilege escalation attacks.
e. Secure Communication
All data transmitted between IoT devices and cloud servers should be encrypted end-to-end, using protocols like TLS 1.3 or DTLS. Zero Trust ensures encryption is enforced even for internal device-to-device communications.
f. Adaptive Policies
Policies must dynamically adjust based on device posture, behavior, or environmental context. For example, a wearable health monitor connecting from an unrecognized network may require additional verification steps before transmitting patient data.
4. Technologies Enabling Zero Trust for IoT
The practical deployment of Zero Trust in IoT ecosystems relies on an array of emerging technologies that complement its philosophy.
- Artificial Intelligence (AI) and Machine Learning (ML): AI enhances Zero Trust by automating threat detection and adapting access controls based on behavioral analysis.
- Blockchain: Distributed ledger technology can provide immutable records for device identity and communication integrity.
- Software-Defined Perimeter (SDP): SDP dynamically creates secure tunnels for authenticated users and devices, effectively hiding critical assets.
- Edge Computing Security: Zero Trust aligns with edge architectures by enforcing policies locally, reducing latency while maintaining strong authentication.
- Secure Access Service Edge (SASE): Integrating Zero Trust with SASE frameworks allows IoT networks to benefit from cloud-native, policy-driven access control.
- Zero Trust Network Access (ZTNA): ZTNA replaces traditional VPNs, offering identity-aware and context-based access to IoT applications and data.
5. Implementing a Zero Trust Framework in IoT
Transitioning to a Zero Trust model in IoT is a gradual process requiring careful planning, integration, and policy definition.
Step-by-Step Implementation:
- Asset Discovery: Identify and classify all IoT devices, data flows, and users.
- Define Trust Boundaries: Determine which systems require isolation and segmentation.
- Establish Strong Identity and Access Management (IAM): Deploy certificate-based or hardware-backed identity systems for device authentication.
- Micro-Segment the Network: Divide devices into logical groups and apply granular access policies.
- Implement Continuous Monitoring: Use analytics to observe traffic patterns, flag anomalies, and ensure compliance.
- Adopt Automation: Utilize AI-driven orchestration tools to enforce dynamic policies in real-time.
- Regular Auditing and Updating: Periodically review access rules, device configurations, and logs to identify vulnerabilities.
6. Benefits of Zero Trust in IoT
- Enhanced Security: Eliminates blind trust, minimizing attack vectors and lateral movement.
- Resilience Against Breaches: Micro-segmentation and least privilege access prevent widespread compromise.
- Compliance and Privacy: Aligns with data protection regulations like GDPR, HIPAA, and NIST standards.
- Operational Visibility: Continuous monitoring provides detailed insights into device health and behavior.
- Scalability: Zero Trust can evolve with IoT growth without compromising control or performance.
7. Challenges in Adopting Zero Trust for IoT
Despite its advantages, implementing Zero Trust in IoT networks presents technical and organizational hurdles:
- Device Constraints: Many IoT devices lack computational power for cryptography or frequent verification.
- Integration Complexity: Retrofitting Zero Trust onto legacy systems requires major architectural redesigns.
- Cost and Scalability: Deploying certificate-based identity and segmentation at scale can be expensive.
- User Experience: Overly strict policies can affect device interoperability and performance.
- Skill Gaps: Organizations often lack the expertise to design and manage Zero Trust frameworks effectively.
However, as cloud providers, IoT platform vendors, and cybersecurity firms continue to develop lightweight Zero Trust solutions, adoption is expected to become easier and more cost-effective.
8. Real-World Applications and Use Cases
- Healthcare: Protecting patient data from compromised wearables and remote sensors.
- Smart Manufacturing: Ensuring machine-to-machine communications are authenticated and tamper-proof.
- Smart Cities: Managing interconnected infrastructure like traffic lights, surveillance, and public utilities under Zero Trust rules.
- Automotive Industry: Safeguarding vehicle telemetry and over-the-air updates from remote attacks.
- Energy Sector: Protecting smart grids from unauthorized access and cyber-physical threats.
These real-world applications demonstrate how Zero Trust can create a resilient foundation for the IoT-driven future.
9. The Future of Zero Trust in IoT
As IoT continues to evolve toward autonomous systems, AI-driven automation, and 6G-connected environments, Zero Trust will become a default security requirement. Future Zero Trust implementations will incorporate quantum-resistant cryptography, AI-led adaptive defense, and blockchain-enabled identity fabrics. Governments and standards bodies, such as NIST and ISO, are already developing frameworks to formalize Zero Trust architectures for IoT and critical infrastructure.
The Internet of Things (IoT) has transformed the modern digital landscape by interconnecting billions of smart devices, from household appliances and wearable sensors to industrial control systems and autonomous vehicles. However, this widespread connectivity has also created an exponentially growing attack surface, where each connected device represents a potential vulnerability. Traditional cybersecurity models, which rely on securing the network perimeter and trusting anything inside it, are proving inadequate in this era of distributed, dynamic, and cloud-driven systems. The concept of Zero Trust Security (ZTS) emerges as a revolutionary solution to these challenges. At its core, Zero Trust is based on the principle of “never trust, always verify.” It eliminates implicit trust within networks and replaces it with continuous authentication, verification, and validation of every user, device, and data flow, regardless of whether they reside inside or outside the network perimeter. For IoT environments, where devices are diverse, resource-constrained, and geographically dispersed, this approach offers a proactive and adaptive method to ensure that only verified entities gain access to sensitive data and operations. Implementing Zero Trust in IoT begins with device identity and authentication, ensuring that every connected component has a unique, verifiable identity through digital certificates, hardware roots of trust, or blockchain-based ledgers. This prevents unauthorized or spoofed devices from entering the network. Micro-segmentation further enhances security by dividing networks into isolated zones, preventing attackers from moving laterally if they breach one segment. In Zero Trust IoT frameworks, communication between devices, cloud systems, and gateways is encrypted end-to-end using protocols like TLS 1.3 or DTLS, ensuring that data integrity and confidentiality remain uncompromised even across open networks. Continuous monitoring powered by artificial intelligence (AI) and machine learning (ML) is another critical component, enabling real-time detection of anomalous behavior such as unusual data transfers, unexpected communication patterns, or unauthorized access attempts. This behavioral analytics-driven vigilance allows organizations to respond instantly to potential breaches. Furthermore, least privilege access ensures that every device or user only has the minimal permissions necessary for its task—significantly reducing the risk of insider threats and privilege escalation attacks. Zero Trust also adopts adaptive policy enforcement, where access decisions are contextually aware, adjusting dynamically based on device health, location, time, and risk score. For instance, an industrial sensor connecting from an unfamiliar network might be temporarily restricted or subjected to additional verification before being granted access. Technologies such as Software-Defined Perimeters (SDP) and Zero Trust Network Access (ZTNA) reinforce these principles by creating invisible, identity-based network boundaries that hide critical assets from unauthorized entities. Blockchain adds transparency and immutability to IoT communication logs and device identities, while edge computing enhances performance by enabling Zero Trust policies to be enforced closer to the devices themselves, reducing latency and dependency on centralized systems. The implementation process typically begins with discovering and classifying all IoT assets, mapping their data flows, and defining trust boundaries. This is followed by establishing a strong Identity and Access Management (IAM) framework, segmenting networks based on device criticality, enforcing strict encryption protocols, and deploying automated threat detection and response mechanisms. The benefits of Zero Trust in IoT are substantial: it enhances overall security posture, prevents large-scale breaches, ensures regulatory compliance (e.g., GDPR, HIPAA, NIST), and improves operational visibility across complex networks. Yet, challenges persist—such as the limited processing power of many IoT devices that cannot support heavy encryption, the difficulty of integrating legacy systems, high implementation costs, and the shortage of skilled cybersecurity professionals. Despite these hurdles, industry momentum is accelerating as lightweight cryptographic techniques, cloud-managed Zero Trust services, and AI-driven orchestration tools evolve. Real-world applications already demonstrate its impact: hospitals using Zero Trust to safeguard remote patient monitoring devices, factories securing machine-to-machine communication, and smart cities protecting interconnected infrastructure from cyber sabotage. The future of Zero Trust in IoT lies in convergence with quantum-resistant cryptography, AI-based adaptive defense systems, and policy frameworks standardized by organizations like NIST and ISO. As 6G, autonomous systems, and intelligent edge computing become mainstream, Zero Trust will transition from a recommended strategy to an essential architectural mandate. Ultimately, Zero Trust Security redefines digital trust by treating every connection as a potential threat and validating it continuously through contextual intelligence. In an increasingly hyperconnected world, where the line between physical and digital domains blurs, Zero Trust offers a robust foundation for building resilience, privacy, and integrity into the very fabric of the Internet of Things.
The Internet of Things (IoT) has fundamentally transformed the way individuals, businesses, and governments interact with the digital world, connecting billions of devices, ranging from smart home appliances, wearable fitness trackers, and healthcare monitoring devices to industrial control systems, autonomous vehicles, and city-wide infrastructure sensors, all of which communicate continuously over networks and generate immense volumes of data, enabling efficiencies, automation, and real-time decision-making that were previously unimaginable, yet at the same time introducing unprecedented security challenges because each connected device represents a potential vulnerability that can be exploited by malicious actors, ranging from individual hackers to sophisticated cybercriminal organizations and even nation-state attackers, particularly since many IoT devices are constrained in terms of processing power, memory, and energy capacity, making it difficult or impossible to implement traditional security measures such as complex encryption algorithms, multi-factor authentication, or frequent software patching, and this problem is exacerbated by the heterogeneity of the IoT ecosystem, where devices often run on diverse operating systems, firmware versions, and communication protocols, creating inconsistent security postures and leaving gaps that attackers can exploit, and as the proliferation of IoT devices accelerates—estimates suggest there will be more than 30 billion devices by 2030—the need for a fundamentally different approach to security becomes not just desirable but essential, which is where the concept of Zero Trust Security becomes particularly relevant, because Zero Trust is a paradigm that operates on the principle of “never trust, always verify,” fundamentally challenging the traditional network security model that relies on a secure perimeter and implicit trust for devices and users within that perimeter, and instead, Zero Trust treats every device, user, and data flow as untrusted by default, requiring continuous verification, strong authentication, and authorization for every interaction, regardless of where the device or user is located, and for IoT networks, this philosophy translates into several practical implementations, beginning with the establishment of a unique, verifiable identity for each device, often using cryptographic methods, public key infrastructure (PKI), hardware roots of trust, or even blockchain-based identity solutions, which ensures that only authorized devices can communicate on the network and prevents rogue devices from initiating connections or exfiltrating data, and this identity framework is complemented by micro-segmentation, where the IoT network is divided into isolated zones, limiting lateral movement so that if one device is compromised, attackers cannot easily access other devices or critical systems, and coupled with least privilege access principles, Zero Trust ensures that devices and users only have access to the specific resources they require for their function, reducing the risk of privilege escalation attacks and minimizing the attack surface, while end-to-end encryption of data in transit and at rest ensures confidentiality and integrity of sensitive information, which is particularly important for IoT applications in healthcare, finance, industrial automation, and critical infrastructure where data breaches can have severe consequences, and these technical safeguards are further reinforced by continuous monitoring and analytics, leveraging artificial intelligence and machine learning to identify anomalous patterns, such as unusual communication attempts, abnormal traffic spikes, or deviations in device behavior, allowing security teams or automated systems to respond in real time, either by alerting administrators or by isolating suspicious devices automatically, and beyond these technological measures, Zero Trust in IoT also involves adaptive policy enforcement, where access decisions are dynamic and context-aware, taking into consideration factors such as device health, location, time, user behavior, and environmental conditions, so for example, a sensor attempting to transmit sensitive industrial data from an unrecognized network may trigger additional verification steps or be temporarily blocked until its legitimacy is confirmed, and the practical deployment of Zero Trust in IoT environments relies on complementary technologies such as Software-Defined Perimeters (SDPs) and Zero Trust Network Access (ZTNA), which create identity-based virtual perimeters around critical resources, effectively hiding them from unauthorized entities and reducing exposure to attacks, while edge computing enables local enforcement of Zero Trust policies, improving performance and reducing latency in large-scale IoT deployments, and blockchain can provide immutable records of device identities and communication histories, enhancing transparency and accountability, and all these measures collectively ensure that IoT networks are resilient, secure, and capable of supporting innovation in sectors ranging from smart homes, healthcare, industrial automation, and transportation to smart cities and energy grids, while at the same time aligning with regulatory requirements such as GDPR, HIPAA, and NIST frameworks by ensuring strict access control, auditability, and data privacy, though implementing Zero Trust in IoT is not without challenges, as organizations face obstacles including the limited computational capabilities of many IoT devices, integration complexities with legacy systems, high deployment costs, and the need for skilled personnel to manage sophisticated security infrastructures, yet despite these hurdles, the adoption of lightweight cryptography, AI-driven automation, cloud-based Zero Trust platforms, and improved industry standards is making it increasingly feasible for enterprises to implement Zero Trust at scale, and real-world applications are already demonstrating its effectiveness, such as hospitals securing remote patient monitoring devices, factories protecting machine-to-machine communications, smart cities safeguarding traffic management systems, and automotive companies ensuring the integrity of vehicle telemetry and over-the-air updates, and looking ahead, the evolution of IoT toward autonomous systems, AI-driven automation, 6G connectivity, and quantum computing will further necessitate Zero Trust approaches, incorporating quantum-resistant cryptography, AI-based adaptive defenses, and blockchain-enabled identity fabrics, ultimately establishing Zero Trust not merely as a security framework but as a foundational architecture for resilient, trustworthy, and future-ready IoT ecosystems, because in an environment where billions of devices interact, where the boundary between physical and digital worlds is increasingly blurred, and where cyber threats are growing in sophistication, adopting a Zero Trust approach ensures that every interaction is validated, every access is justified, and every system is protected, transforming the security landscape from reactive defense to proactive assurance and providing the foundation for a hyperconnected world where trust is earned continuously rather than assumed.
Conclusion
Zero Trust Security represents a paradigm shift in how we secure IoT ecosystems. In a world where billions of devices interact across open networks, the concept of a trusted perimeter is obsolete. By enforcing continuous verification, least privilege access, micro-segmentation, and adaptive policy enforcement, Zero Trust transforms IoT security from reactive defense to proactive assurance.
While implementation challenges exist—such as scalability, device limitations, and integration complexity—the long-term benefits in security, compliance, and resilience far outweigh these barriers. As industries, governments, and consumers embrace IoT innovations, Zero Trust stands as the cornerstone of a secure, interconnected future.
Q&A Section
Q1: What is the core principle of Zero Trust Security?
Ans: Zero Trust Security operates on the principle of “never trust, always verify.” It requires continuous authentication and authorization of every device, user, and connection, regardless of whether it is inside or outside the network.
Q2: Why is Zero Trust especially important for IoT networks?
Ans: IoT networks consist of billions of devices, many with weak or no security. Zero Trust ensures each device and connection is continuously verified, minimizing risks from unauthorized access and preventing breaches from spreading.
Q3: How does micro-segmentation help in Zero Trust IoT security?
Ans: Micro-segmentation divides the IoT network into isolated zones. If one device or segment is compromised, it cannot infect or access others, effectively containing potential attacks.
Q4: What technologies enable Zero Trust in IoT environments?
Ans: Key enablers include AI and machine learning for behavior analysis, blockchain for device identity, software-defined perimeters (SDP), Zero Trust Network Access (ZTNA), and edge computing for local policy enforcement.
Q5: What are the main challenges in implementing Zero Trust for IoT?
Ans: Challenges include limited device processing power, high deployment costs, legacy system integration issues, and the need for skilled personnel to design and manage the framework.
Similar Articles
Find more relatable content in similar Articles

How Blockchain Is Reinventing ..
Blockchain is transforming cyb.. Read More

Wearable Health Sensors: The D..
Wearable health sensors are re.. Read More
Why Mesh Networks Might Replac..
Mesh networks are transforming.. Read More

Foldable Screens in 2025: Are ..
Foldable screens have finally .. Read More
Explore Other Categories
Explore many different categories of articles ranging from Gadgets to Security
Smart Devices, Gear & Innovations
Discover in-depth reviews, hands-on experiences, and expert insights on the newest gadgets—from smartphones to smartwatches, headphones, wearables, and everything in between. Stay ahead with the latest in tech gear
Apps That Power Your World
Explore essential mobile and desktop applications across all platforms. From productivity boosters to creative tools, we cover updates, recommendations, and how-tos to make your digital life easier and more efficient.
Tomorrow's Technology, Today's Insights
Dive into the world of emerging technologies, AI breakthroughs, space tech, robotics, and innovations shaping the future. Stay informed on what's next in the evolution of science and technology.
Protecting You in a Digital Age
Learn how to secure your data, protect your privacy, and understand the latest in online threats. We break down complex cybersecurity topics into practical advice for everyday users and professionals alike.
© 2025 Copyrights by rTechnology. All Rights Reserved.