
Zero-Trust Security Models: Are Traditional Firewalls Dead?
As cyber threats evolve and network perimeters dissolve, traditional firewalls are no longer sufficient on their own. This article explores the rise of Zero-Trust Security Models, a modern framework built on continuous verification, least-privilege access, and identity-centric controls. Discover how Zero Trust transforms cybersecurity and whether firewalls still have a role in today’s security landscape.
✨ Raghav Jain
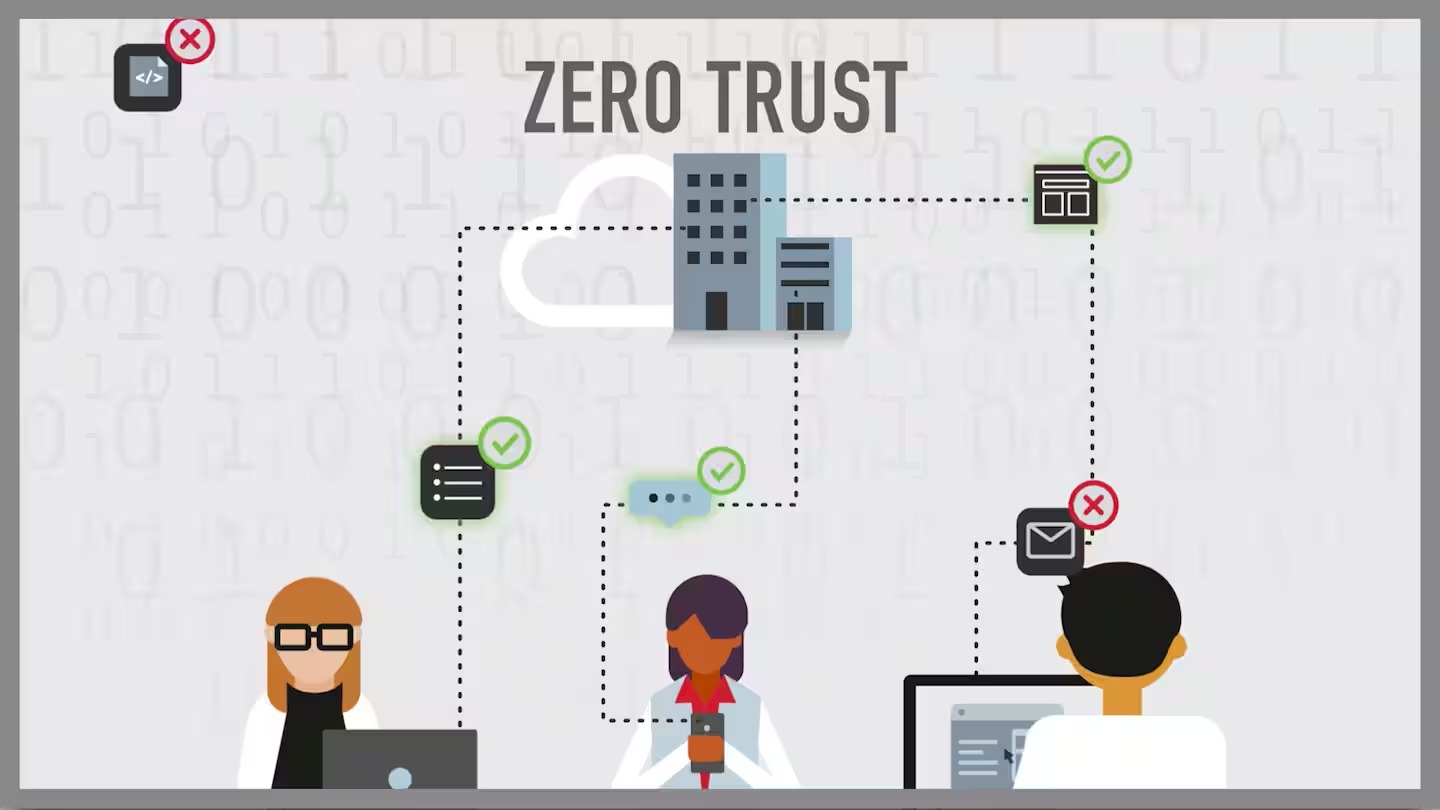
Introduction: The Changing Landscape of Cybersecurity
In a time when businesses are rapidly embracing digital transformation, cloud computing, and remote work environments, cybersecurity is under more pressure than ever before. Traditional perimeter-based defenses, such as firewalls, once stood as the cornerstone of enterprise security. These mechanisms were designed to keep the bad guys out and the good guys in—assuming trust inside the perimeter.
However, in today's hyper-connected world, that perimeter is blurred. Employees access networks from coffee shops, cyber attackers impersonate insiders, and third-party vendors often have elevated access. This evolving threat landscape has exposed the limitations of traditional firewalls and catalyzed the rise of Zero-Trust Security Models.
But does this mean that traditional firewalls are obsolete? Let’s explore the fundamentals of Zero Trust, compare it with traditional approaches, assess its benefits and challenges, and determine whether firewalls still hold any relevance.
What is a Zero-Trust Security Model?
Zero Trust is not a specific product or technology, but rather a comprehensive security framework based on a simple principle: “Never trust, always verify.” Regardless of whether a user or device is inside or outside the network, access is not granted by default. Instead, continuous authentication, authorization, and validation of every request are mandated.
Core principles of Zero Trust:
- Verify Explicitly: Authenticate and authorize based on all available data points, such as user identity, location, device health, and workload.
- Use Least Privilege Access: Limit user access to only what is strictly necessary for their role.
- Assume Breach: Operate with the mindset that the network has already been compromised, and segment accordingly.
- Microsegmentation: Divide the network into granular zones to contain breaches.
- Continuous Monitoring: Analyze logs, behaviors, and anomalies in real-time.
Zero Trust is not a "rip-and-replace" model; rather, it is often implemented in layers on top of or alongside existing infrastructure.
Traditional Firewalls: A Brief Overview
Firewalls have long been the front line of cybersecurity, filtering traffic based on predefined security rules. These are broadly categorized into:
- Packet-filtering firewalls
- Stateful inspection firewalls
- Proxy firewalls
- Next-generation firewalls (NGFWs)
They monitor traffic entering and exiting a trusted internal network and aim to block malicious traffic based on IP addresses, ports, and protocols.
While traditional firewalls still play a role in some aspects of network security, they largely trust internal traffic and assume that anything within the corporate perimeter is safe. This trust model creates vulnerabilities when attackers breach the perimeter or when insiders act maliciously.
Zero Trust vs. Traditional Firewall Security
Feature/Concept Traditional Firewalls Zero-Trust Security Trust Model Implicit trust inside the perimeter Zero trust everywhere Network Perimeter Strong reliance Perimeter-less or micro-perimeters Authentication Usually at initial entry Continuous and contextual Device Trust Minimal verification Device posture is evaluated Lateral Movement High risk if breached Restricted via microsegmentation Cloud & Remote Work Limited compatibility Natively cloud and remote-friendly Scalability Rigid, hardware-based Software-defined, scalable
The Modern Threat Landscape Driving Zero Trust
Several developments in the cyber world have rendered traditional defenses insufficient:
- Cloud Migration: Applications and data reside in multiple clouds, beyond the firewall’s reach.
- Remote Work: Employees work from home or travel, accessing systems through personal or unsecured devices.
- BYOD Culture: Employees use personal devices, increasing attack surfaces.
- Advanced Threats: Sophisticated attackers bypass firewalls through phishing, stolen credentials, or supply chain attacks.
- Insider Threats: Malicious or careless insiders can cause breaches from within the firewall perimeter.
These trends necessitate a model that secures individual assets, devices, and users rather than relying on a central gatekeeper.
Key Technologies Behind Zero Trust
Zero Trust isn't a single product but a combination of technologies and strategies:
- Identity and Access Management (IAM): Centralized identity control ensures only authenticated users access resources.
- Multi-Factor Authentication (MFA): Adds a second layer of protection beyond passwords.
- Endpoint Detection and Response (EDR): Monitors and responds to threats at the device level.
- Security Information and Event Management (SIEM): Aggregates and analyzes data logs for real-time insights.
- Software-Defined Perimeters (SDP): Dynamically creates secure connections based on identity and context.
- Microsegmentation: Enforces policies on data flows within the network, limiting lateral movement.
Implementing a Zero Trust Model
Transitioning to Zero Trust is a journey, not a single switch. Here’s a phased approach:
- Define the Protect Surface: Focus on data, applications, assets, and services (DAAS).
- Map the Transaction Flows: Understand how data moves across your organization.
- Build Micro-Perimeters: Use technologies like NGFWs, SDPs, or cloud-native firewalls for segmentation.
- Enforce Zero Trust Policies: Use identity and context to strictly enforce access.
- Continuously Monitor: Apply AI/ML tools to detect anomalies and refine rules.
Challenges and Considerations
Implementing Zero Trust isn’t without its hurdles:
- Complexity: Requires deep understanding of organizational workflows and applications.
- Cost: Initial deployment may involve investment in new tools, infrastructure, and training.
- User Friction: Continuous authentication can affect user experience if not done smartly.
- Legacy Systems: Older systems may not be compatible with modern Zero Trust principles.
Despite these, the long-term gains in security posture, visibility, and adaptability far outweigh the initial challenges.
Are Firewalls Really Dead?
No—but they are evolving.
Firewalls are not obsolete, but their role has shifted. Modern Next-Gen Firewalls (NGFWs) can be part of a Zero Trust architecture by providing deep packet inspection, application-layer filtering, and threat intelligence integration.
In cloud-native environments, firewalls are virtualized and tied to identity and context. In this way, the firewall becomes just one control point among many in a broader Zero Trust framework.
So, while the old model of relying only on firewalls for security is dead, firewalls as adaptable components within a Zero Trust ecosystem are very much alive.
In today’s rapidly evolving digital world, where cloud computing, remote work, and distributed environments have become the new norm, the traditional perimeter-based cybersecurity model is increasingly being called into question. Historically, firewalls were the gold standard of network security, operating on the assumption that threats existed only outside the corporate network while everything within was inherently trustworthy. These firewalls filtered traffic based on IP addresses, ports, and protocols and created a hardened perimeter, likened to a fortress wall protecting a castle. However, with the rise of software-as-a-service (SaaS) platforms, bring-your-own-device (BYOD) policies, mobile workforces, and hybrid cloud infrastructures, the corporate perimeter is dissolving, making traditional firewalls inadequate to address modern threats. Enter the Zero-Trust Security Model—a transformative approach that ditches the outdated idea of inherent trust. Zero Trust operates on a foundational principle: “Never trust, always verify.” This means that regardless of whether access requests come from inside or outside the network, they must be thoroughly authenticated, authorized, and continuously validated before being allowed. Unlike traditional models that focus on defending the network’s borders, Zero Trust focuses on securing individual resources, users, and workloads. It assumes that breaches are inevitable—or may have already occurred—and hence, it insists on validating every user, device, and connection every time. This shift becomes particularly crucial when one considers the sheer volume of sophisticated cyberattacks exploiting remote access, phishing, compromised credentials, and supply chain vulnerabilities. Zero Trust’s architecture integrates various components like Identity and Access Management (IAM), Multi-Factor Authentication (MFA), Endpoint Detection and Response (EDR), encryption, microsegmentation, behavior analytics, and continuous monitoring. These tools work in harmony to verify identity, assess device health, and grant least-privilege access, all while monitoring for anomalous activity. Microsegmentation, in particular, plays a vital role by dividing networks into small, manageable zones, ensuring that even if a breach occurs, its spread is contained. Unlike firewalls that offer perimeter protection, microsegmentation limits lateral movement, a common tactic used by attackers post-breach. Moreover, Zero Trust aligns well with cloud-native infrastructures, where users and data are scattered across multiple geographies and platforms, making it nearly impossible to draw a clear security perimeter. Traditional firewalls, even when upgraded to next-generation versions with advanced threat detection capabilities, still rely heavily on location-based trust and often fall short in a world where identity is the new perimeter. This doesn’t mean firewalls are entirely obsolete; rather, they need to evolve and integrate into the Zero Trust ecosystem. Many modern Next-Generation Firewalls (NGFWs) support application-layer filtering, intrusion prevention, and cloud-based threat intelligence, and when combined with Zero Trust principles, can still contribute value by enforcing granular access controls and traffic segmentation. The question, then, isn't whether firewalls are dead, but whether we can continue to depend on them as the cornerstone of network security—and the answer is increasingly a resounding no. Instead, organizations are moving toward a model where firewalls are just one part of a broader, more intelligent, and identity-driven security framework. Implementing Zero Trust isn’t a plug-and-play solution; it requires a strategic approach that begins with identifying critical assets (data, applications, services) and understanding how they interact. Once these protect surfaces are mapped, security teams can build policies based on context—who is requesting access, from where, using what device, and under what conditions. Access is granted only after successful validation of all parameters, and is continuously re-evaluated throughout the session. However, transitioning to Zero Trust is not without challenges. It demands an overhaul of existing IT infrastructure, integration with legacy systems, adoption of cloud-native tools, and a cultural shift in how organizations view security. The cost and complexity involved can be significant, especially for large enterprises with vast, decentralized networks. Additionally, over-restricting access or misconfiguring policies can lead to user frustration or business disruption. Thus, a phased implementation approach—starting small and expanding gradually—is often recommended. Despite these challenges, the advantages are compelling: enhanced visibility, reduced attack surface, greater compliance with data protection regulations, and improved resilience against insider threats and credential-based attacks. In fact, industry leaders and government bodies are already advocating for Zero Trust as a standard security model. The U.S. federal government, for example, issued an executive order mandating federal agencies to adopt Zero Trust architectures. Technology giants like Google and Microsoft have also embedded Zero Trust into their internal and external security offerings. The growing consensus is clear: in a landscape where trust is a vulnerability, a Zero Trust approach is not just an upgrade—it’s a necessity. To summarize, while firewalls are not entirely dead, their function has dramatically changed. The concept of relying solely on a network perimeter to secure an organization is outdated and dangerous in the face of modern threats. Zero Trust doesn’t eliminate firewalls but redefines their role within a broader, more dynamic, and decentralized security strategy. It replaces static, location-based controls with adaptive, identity-driven policies that offer better protection in a world without borders. Organizations aiming for robust cybersecurity must move beyond perimeter defenses and embrace a Zero Trust mindset—one where trust is never assumed, and verification is always enforced.
In the ever-evolving landscape of cybersecurity, the concept of “Zero-Trust Security” has emerged as both a revolutionary framework and a necessary response to the inadequacies of traditional perimeter-based defense models, particularly the reliance on firewalls. Traditionally, firewalls were deployed as the central line of defense, establishing a secure perimeter between an organization’s internal network and the external world. This approach operated on the assumption that internal users and devices could be trusted by default, while anything outside that boundary was considered potentially hostile. For years, this model served as the bedrock of enterprise security, effectively protecting on-premises infrastructure in centralized environments. However, the digital transformation of the last decade—marked by the proliferation of cloud computing, remote work, mobile access, Internet of Things (IoT) devices, and bring-your-own-device (BYOD) policies—has rendered this security paradigm not only outdated but dangerously insufficient. The modern enterprise has no clear perimeter; employees access critical systems from cafés, hotel rooms, and personal smartphones, while data moves fluidly across multi-cloud platforms, SaaS applications, and hybrid environments. In this context, the traditional firewall struggles to identify legitimate traffic, especially when attackers can exploit compromised credentials or leverage internal vulnerabilities to move laterally once inside. This shift in the threat environment has driven the rise of Zero-Trust Security Models, which rest on a fundamentally different philosophy: “Never trust, always verify.” In a Zero Trust architecture, no user or device is inherently trusted—regardless of whether they are inside or outside the traditional network boundary. Every access request is subject to strict identity verification, contextual analysis, and continuous authentication, ensuring that access is granted only when it is explicitly justified. Zero Trust relies heavily on a range of integrated technologies such as identity and access management (IAM), multi-factor authentication (MFA), endpoint detection and response (EDR), microsegmentation, behavioral analytics, and cloud access security brokers (CASBs). These components work together to assess risk, enforce least-privilege access, monitor for anomalies, and contain breaches before they spread. Unlike firewalls that apply broad, static rules at the network’s edge, Zero Trust enables highly granular, dynamic access control tailored to each user, device, and workload. One of the most transformative aspects of Zero Trust is its compatibility with today’s cloud-native, decentralized infrastructures. Since Zero Trust does not depend on location or network topology, it fits naturally into ecosystems where users and assets are distributed across various platforms and geographies. Security is tied to identity and behavior, not to IP addresses or physical proximity. For example, a user logging in from a known device in their regular location might receive seamless access, while the same user accessing from a suspicious location or unknown device would face additional verification steps—or be denied access entirely. This context-aware approach dramatically reduces the attack surface and helps organizations protect against sophisticated threats such as insider attacks, ransomware, supply chain compromises, and zero-day exploits. However, implementing Zero Trust is not without challenges. It is not a single product or a simple switch that organizations can flip overnight. Rather, it is a comprehensive, strategic shift in how security is conceptualized and operationalized. Organizations must start by identifying their most valuable assets—often referred to as the “protect surface”—and then map the data flows between users, applications, and systems. From there, security policies can be created based on identity, role, device posture, location, time, and risk signals. Microsegmentation is a key component of this effort, as it involves dividing the network into smaller zones where access between zones is tightly controlled. This not only limits lateral movement but also allows faster containment in case of a breach. Continuous monitoring and telemetry gathering ensure that policies are enforced consistently and adapted as new threats emerge. While Zero Trust provides a more robust security posture, it does not necessarily render firewalls obsolete. Instead, it redefines their role. Next-generation firewalls (NGFWs), which offer deep packet inspection, application-layer filtering, and integration with identity systems, can function as policy enforcement points within a Zero Trust architecture. In cloud environments, virtual firewalls can be embedded into workloads to perform inspection and segmentation duties, complementing identity-based controls. Thus, firewalls are not dead—but their function is no longer central or exclusive. In a Zero Trust world, the focus shifts from the network perimeter to the data itself, wherever it resides. Firewalls now operate as one layer among many, rather than being the primary gatekeeper. Moreover, organizations must prepare for the cultural and operational shift that Zero Trust demands. IT teams must break down silos, work cross-functionally with security operations, and invest in employee training to minimize disruption. User experience must also be carefully managed—excessive friction in access control can lead to workarounds or dissatisfaction. Fortunately, modern Zero Trust platforms use AI and machine learning to reduce friction by adapting authentication requirements to risk context. For instance, a trusted user may enjoy passwordless access under normal conditions but be required to complete MFA when unusual behavior is detected. As more organizations adopt Zero Trust, industry best practices, regulatory frameworks, and vendor ecosystems are also evolving to support implementation. Governments are pushing adoption, with mandates like the U.S. Executive Order on Improving the Nation’s Cybersecurity emphasizing Zero Trust principles across federal agencies. Enterprises like Google (with its BeyondCorp model) and Microsoft (with Azure Active Directory conditional access) have pioneered large-scale Zero Trust deployments that now inform broader industry standards. To conclude, while traditional firewalls are far from useless, they are no longer sufficient to protect today’s highly dynamic, perimeterless digital environments. The idea that a single barrier can defend a network has proven ineffective against advanced threats that bypass perimeters with ease. Zero Trust is not just an improvement—it is a necessary evolution in cybersecurity strategy, one that assumes compromise and builds resilience through verification, least privilege, segmentation, and real-time visibility. Organizations that cling to a firewall-centric model without adopting Zero Trust principles expose themselves to unnecessary risk. Conversely, those that embrace Zero Trust as a guiding philosophy will be far better equipped to protect their data, users, and systems in an era defined by complexity, mobility, and constant threat.
Conclusion
- Zero Trust security models reject the notion of a trusted internal network and demand continuous verification and least privilege access.
- Traditional firewalls, while still relevant, are no longer sufficient alone to protect modern networks.
- A hybrid approach, where firewalls are integrated into a Zero Trust framework, offers the best of both worlds.
- Organizations must embrace identity-centric, data-driven, and cloud-compatible security strategies to stay ahead.
- Transitioning to Zero Trust takes time, planning, and investment but is critical to long-term cybersecurity resilience.
Q&A Section
Q1 :- What is the main principle of Zero Trust security?
Ans:- The core principle is “Never trust, always verify.” Every access request must be authenticated and authorized, regardless of its origin.
Q2 :- Are firewalls obsolete in a Zero Trust model?
Ans:- No, firewalls are not obsolete but must evolve. They play a supporting role in Zero Trust by enforcing microsegmentation and contextual filtering.
Q3 :- What are the key components required to implement Zero Trust?
Ans:- Identity and Access Management (IAM), Multi-Factor Authentication (MFA), Endpoint Detection and Response (EDR), microsegmentation, and continuous monitoring.
Q4 :- Why is Zero Trust better for remote work and cloud environments?
Ans:- Zero Trust doesn’t rely on network perimeters. It verifies every user and device regardless of location, making it ideal for remote access and cloud-native operations.
Q5 :- Is Zero Trust a product or a strategy?
Ans:- Zero Trust is a strategic security framework, not a single product. It involves adopting a set of tools and practices that enforce continuous verification and least privilege access.
Similar Articles
Find more relatable content in similar Articles

Wearable Health Sensors: The D..
Wearable health sensors are re.. Read More

Digital DNA: The Ethics of Gen..
Digital DNA—the digitization a.. Read More

Protecting Kids in the Digital..
In an increasingly connected w.. Read More

Data Centers and the Planet: M..
As cloud computing becomes the.. Read More
Explore Other Categories
Explore many different categories of articles ranging from Gadgets to Security
Smart Devices, Gear & Innovations
Discover in-depth reviews, hands-on experiences, and expert insights on the newest gadgets—from smartphones to smartwatches, headphones, wearables, and everything in between. Stay ahead with the latest in tech gear
Apps That Power Your World
Explore essential mobile and desktop applications across all platforms. From productivity boosters to creative tools, we cover updates, recommendations, and how-tos to make your digital life easier and more efficient.
Tomorrow's Technology, Today's Insights
Dive into the world of emerging technologies, AI breakthroughs, space tech, robotics, and innovations shaping the future. Stay informed on what's next in the evolution of science and technology.
Protecting You in a Digital Age
Learn how to secure your data, protect your privacy, and understand the latest in online threats. We break down complex cybersecurity topics into practical advice for everyday users and professionals alike.
© 2025 Copyrights by rTechnology. All Rights Reserved.